LuminanceLabel - Animated overlay and on-screen luminance measurements
Demonstration video on youtube
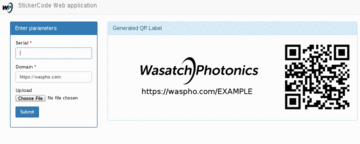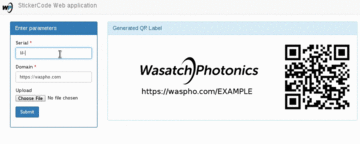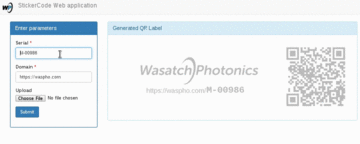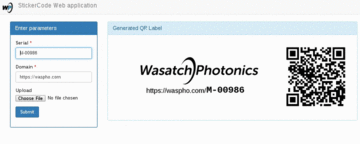
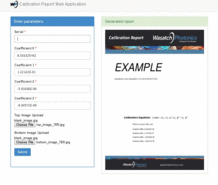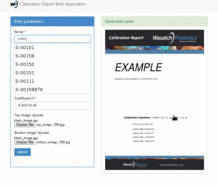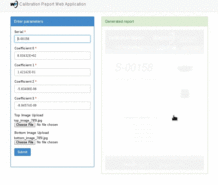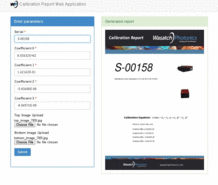
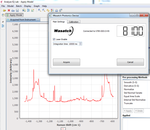
Uses PyQt to place a transparent overlay on the screen, takes a screenshot and processes the area underneath the overlay designator. Luminance values are computed and displayed on the label, and written to stdout.
This is used for evaluting the displayed imagery at multiple frames per …